#0. Overview of the Lab
.png)
VMs
- pfSense
- kali
- SecurityOnion
- Windows
- Linux (optional)
Network subnets
| Network Name | Machine | Subnet |
|---|---|---|
| Green | Windows, Linux | 10.10.10.100/24 |
| Blue | Security Onion | 10.10.20.100/24 |
| Red | Kali | 10.10.30.100/24 |
| VPN | Host machine | 10.10.3.2/24 |
System resources
| VM | RAM (GB) | CPU Cores | ROM (GB) |
|---|---|---|---|
| SecurityOnion | 8 | 4 | 90 |
| Kali | 2 | 2 | VM image (80) |
| Windows LTSC | 2 | 2 | 25 |
| pfSense | 1 | 1 | 20 |
My setup
- Host machine OS: ArchCraft
- RAM: 14 Gigs
- Processor: Ryzen 5 (8 cores)
- Hypervisor: virt-manager/KVM
- ROM: 256 SSD
⚠️ Notes from my side
I suggest you to go through the full setup notes before proceeding, it could clear any doubts when setting it up.
Sometimes, all configuration looks good, but things don't work as they should be, just restart the VMs (literally)
I enabled ssh on all VMs for easy troubleshooting.
#1 Networking
Assign these bridges to your VMs
Use the bridge setup script
The order of bridging interfaces doesn’t matter, but here’s a recommended setup.
-
pfSense VM interfaces:
- WAN →
NATto host machine - LAN →
br-green - OPT1 →
br-blue - OPT2 →
br-red - OPT3 →
VPN - OPT4 →
br-mon(SPAN port)
- WAN →
Configure pfSense
- DHCP : To assign IPs automatically to the connected VMs
- OpenVPN : To access VMs without NAT-ing to host machine.
- DNS
- Firewall : To allow VPN clients
Interfaces
- OPT5, OPT3 are assigned but not enabled.
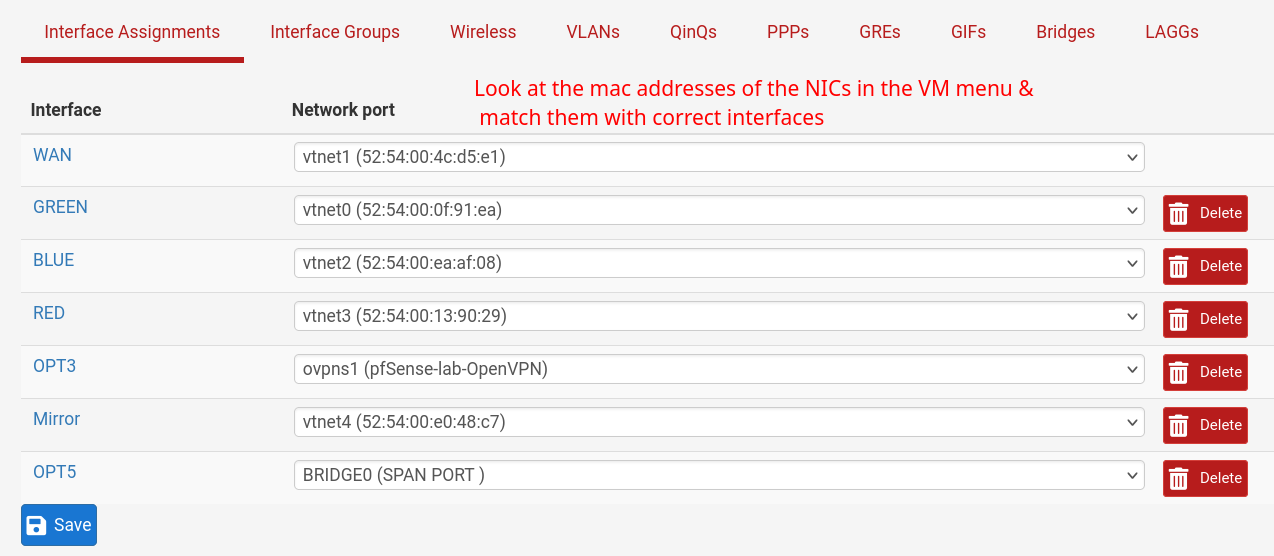
Example
- I chose same mac address as Network port above in configuring GREEN interface
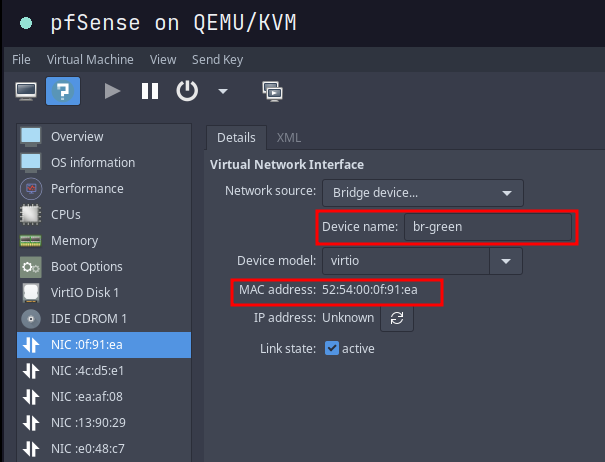
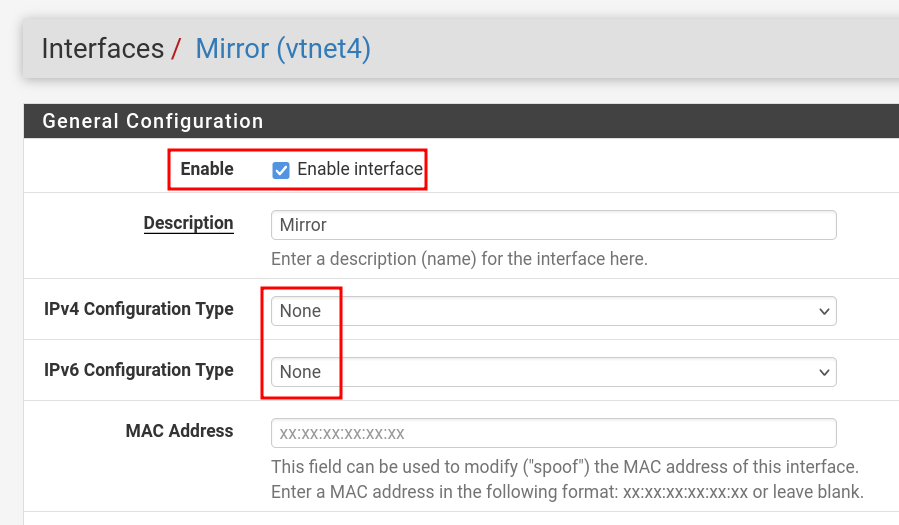
Configure Mirroring/SPAN port on pfSense
- Rename one of the interfaces as Mirror and connect it to bridge
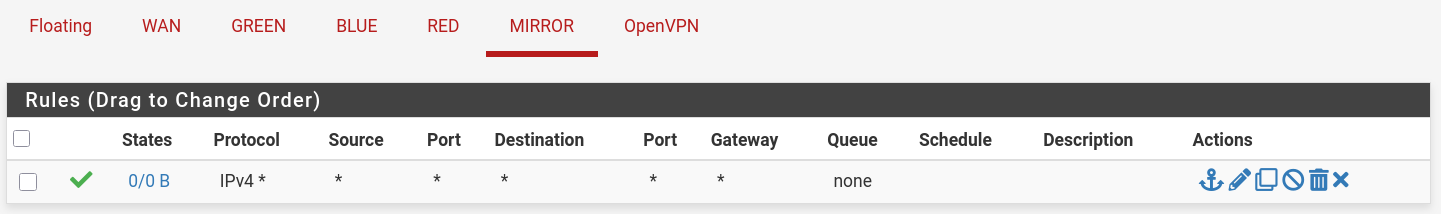
br-mon. - We're using pfSense to perform software-based port mirroring (SPAN), duplicating traffic from specific interfaces (GREEN) to a monitoring interface (OPT4 → br-mon) for analysis.
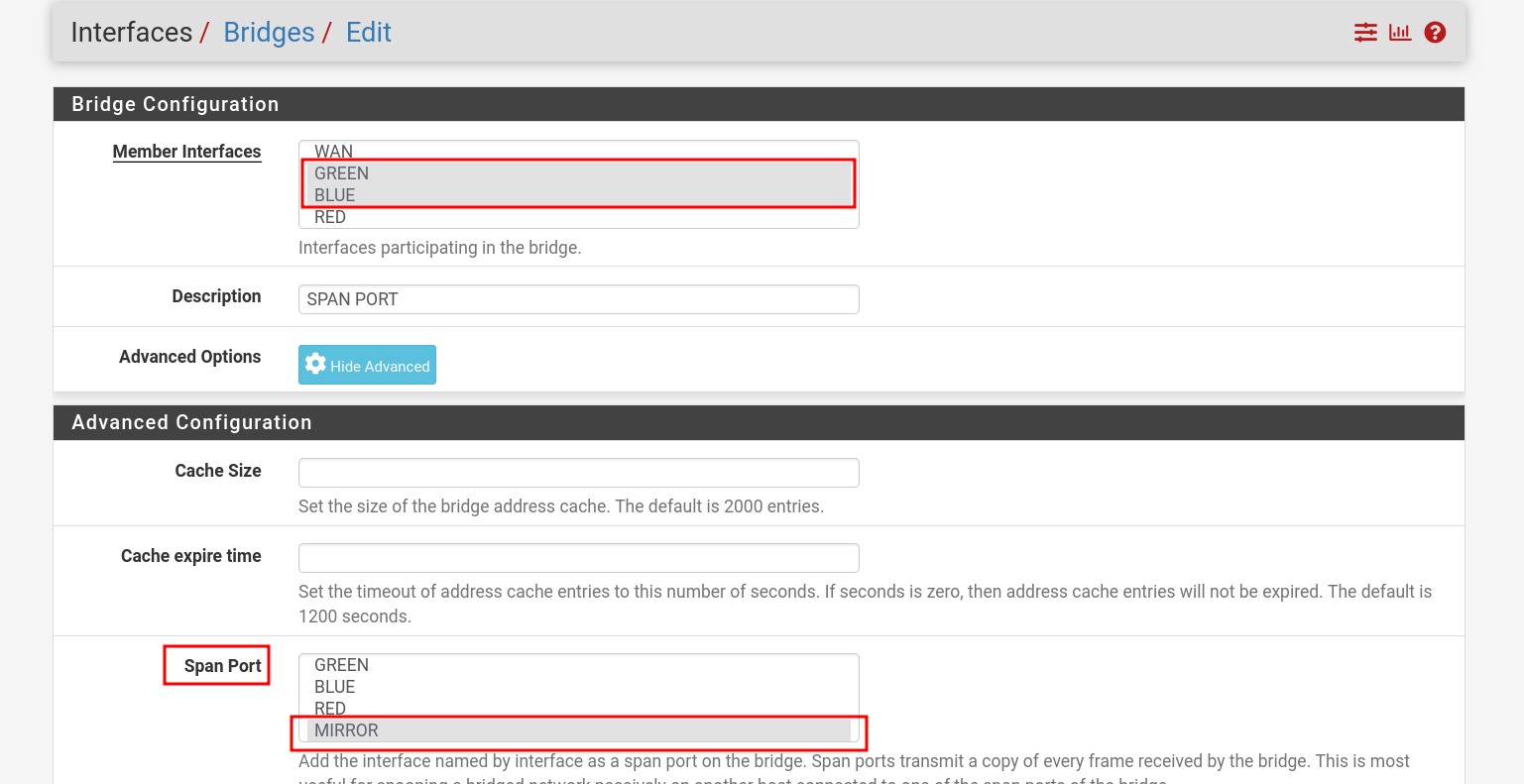
- Go to : Interfaces → Bridges.
- Click on Advanced Options.
Firewall Rules
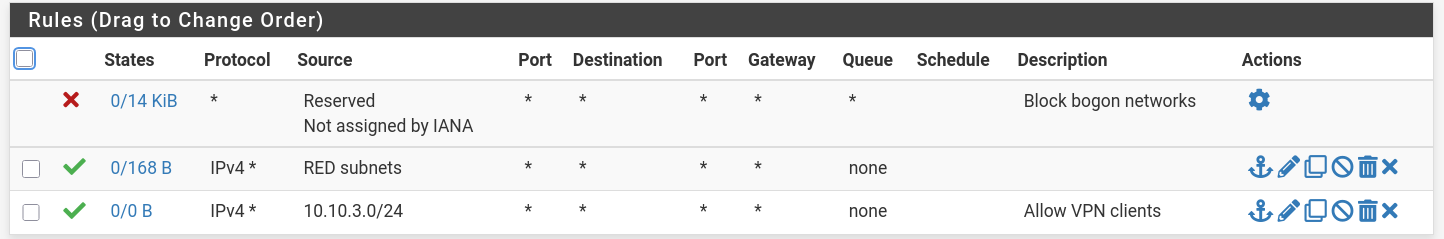
- I gave VPN access to all subnets, so I can ssh and troubleshoot easily.
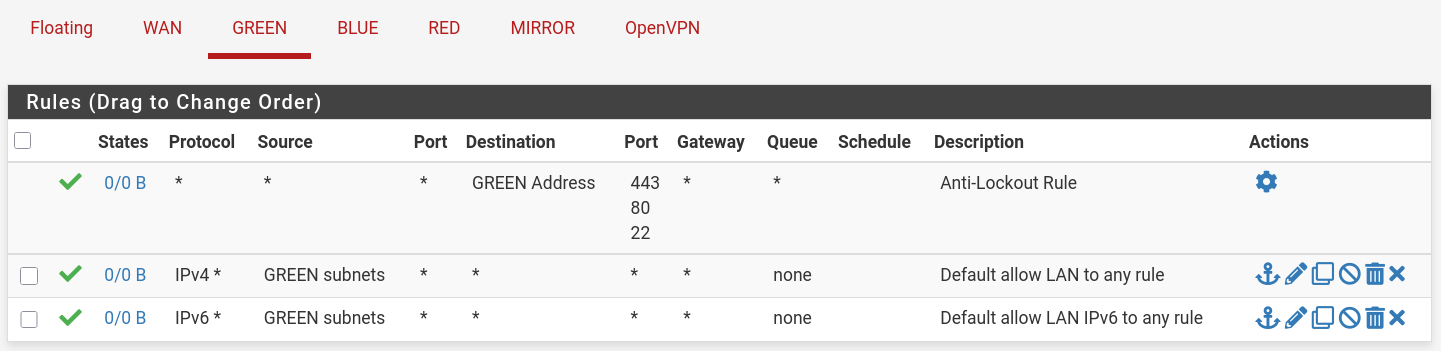
GREEN
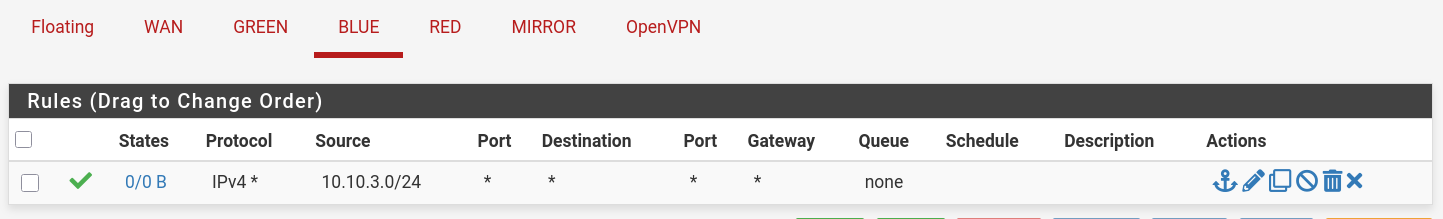
BLUE
RED
Mirror
VPN
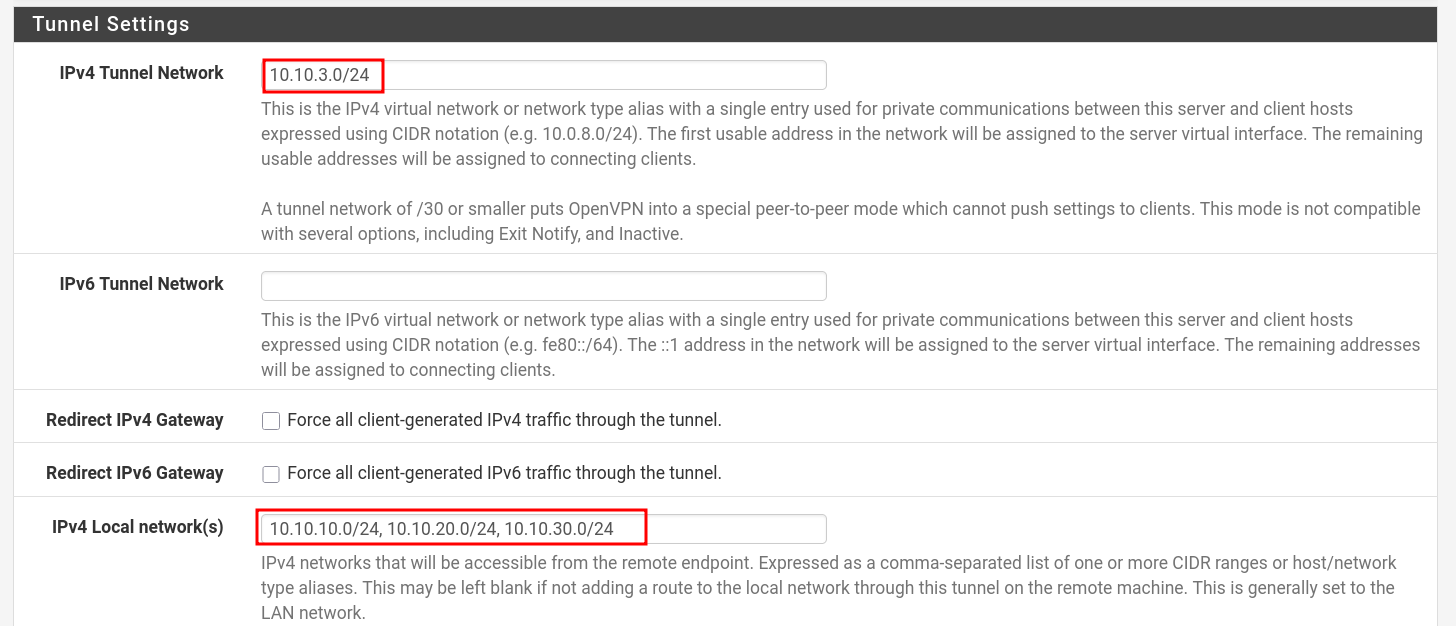
- When setting up your VPN make sure you have a setting to access internal network subnets. Configure it in VPN servers.
- Go to : VPN → OpenVPN → Servers
#2 Security Onion
- There are a few caveats to be addressed in our setup.
- Make sure you have network mirroring working.
Iptables
- This one took me literally 2 days, I think, to get it right, because I tried messing with iptables manually from cli. It was a pain.
- Stop iptables:
sudo systemctl stop iptables
- Now you can access the soc platform on the host machine:
10.10.20.100(I also reserved static ip on the pfsense via DHCP Static Mappings) - Follow this guide: https://docs.securityonion.net/en/2.4/firewall.html#configuring-host-firewall
- For some reason after starting iptables, if you still don't access, restart the VM.
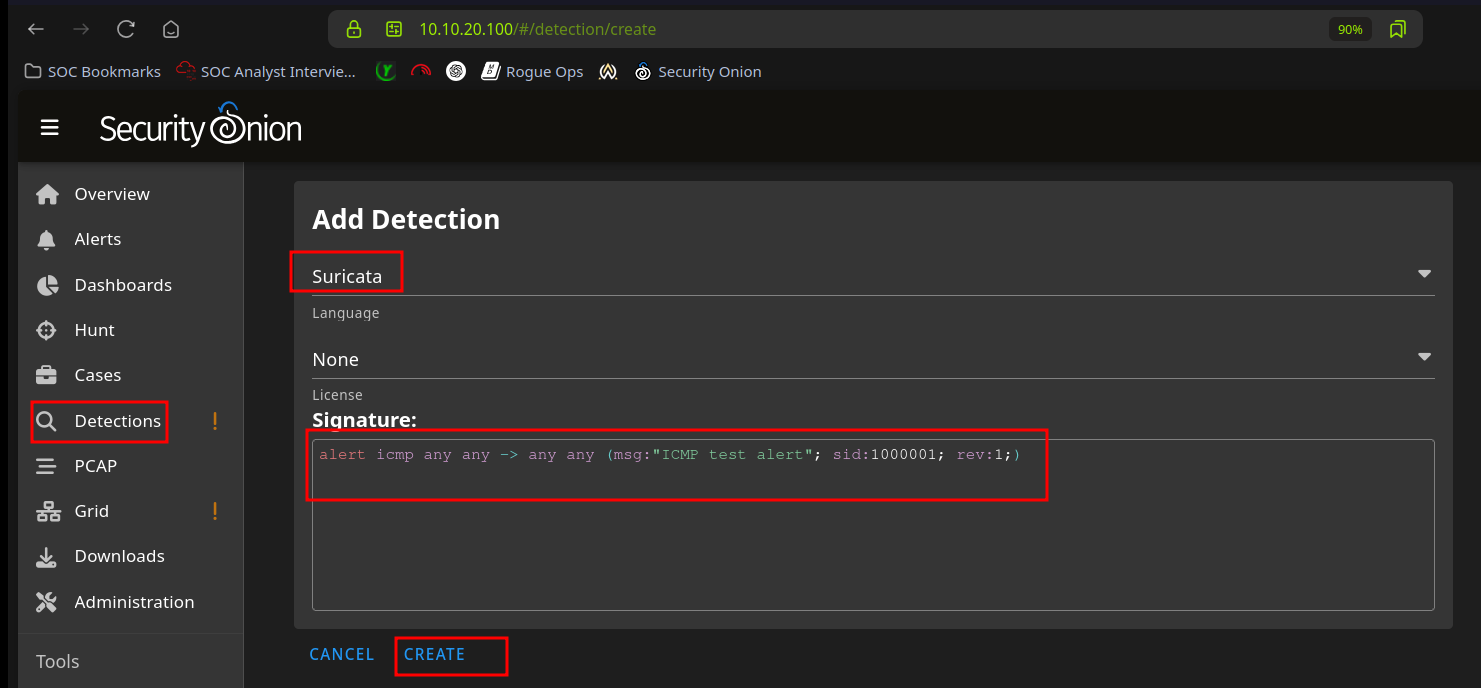
Test suricata alert
- Create ICMP test alert
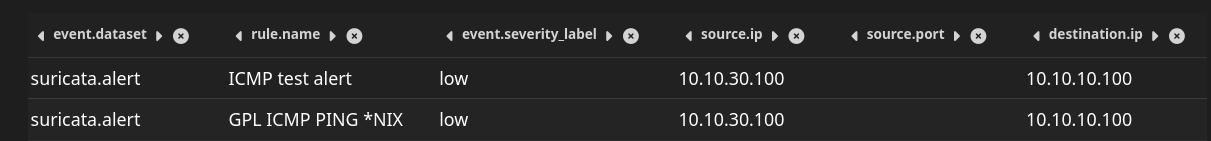
- ping from a red machine to green machine. It can take few mins before it shows up in alerts.
ping -c4 -4 10.10.10.100 # from kali
#3 Scripts to make life easy
I have these script in ~/.custom-scripts-bin. I also added that path to $PATH in .zshrc
- pfsense_vm : start pfsense vm from cli
- setup_bridges_soc : creates and runs bridges
- kali_vm : start kali vm from cli
- SecurityOnion : runs setup_bridges_soc, pfsense_vm, start securityonion from cli
- connect_VPN : simple script to connect to vpn
setup_bridges_soc
#!/bin/bash
# List of bridge names
BRIDGES=("br-green" "br-blue" "br-red" "br-mon")
for BR in "${BRIDGES[@]}"; do
# Check if bridge already exists
if ip link show "$BR" &>/dev/null; then
echo " $BR already exists, skipping."
continue
fi
# Create the bridge
sudo ip link add name "$BR" type bridge
# Bring the bridge up
sudo ip link set "$BR" up
done
kali_vm
- vm name should be
kali
#!/usr/bin/bash
virsh --connect qemu:///system start kali
pfsense_vm
- vm name should be
pfsense
#!/usr/bin/bash
setup_bridges_soc
virsh --connect qemu:///system start pfSense
SecurityOnion
- vm name should be
SecurityOnion
#!/usr/bin/bash
setup_bridges_soc
pfsense_vm
virsh --connect qemu:///system start SecurityOnion
PATH
export PATH=$PATH:$HOME/.custom-scripts-bin/