Detect user account creation and deletion events in Windows environments
Check User Account Audit Policy
AuditPol /get /category:"Account Management"
System audit policy
Category/Subcategory Setting
Account Management
Computer Account Management No Auditing
Security Group Management Success
Distribution Group Management No Auditing
Application Group Management No Auditing
Other Account Management Events No Auditing
User Account Management Success <------ This should be success
Audit computer account management
AuditPol /set /subcategory:"Computer Account Management" /success:enable /failure:enable
🧪 Validation Steps
- Perform a test:
- Create a test user:
net user testuser Test123! /add - Delete it:
net user testuser /del
- Create a test user:
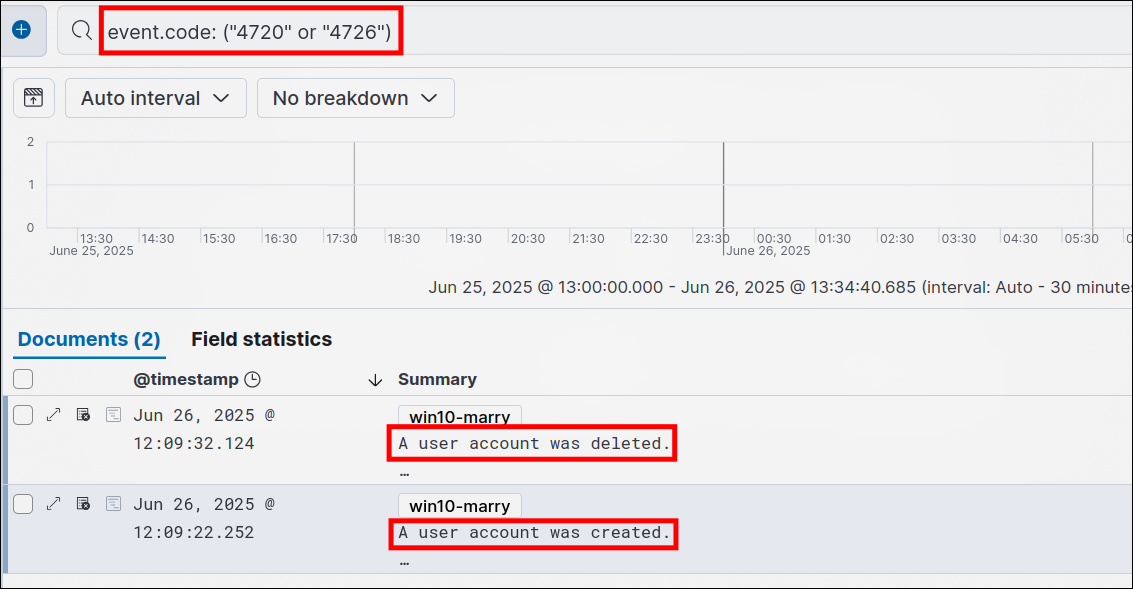
- Kibana -> Discover:
event.code: ("4720" or "4726")
Event IDs to Monitor
Account Creation
Event ID 4720: A user account was created.Event ID 4741: A computer account was created.
Account Deletion
Event ID 4726: A user account was deleted.Event ID 4743: A computer account was deleted.
Optional Auditing Events
Event ID 628/624— legacy versions (Windows Server 2003).Event ID 1102: Audit log cleared (can indicate tampering).